Report: “Taking the Pulse of Hacking: A Risk Basis for Security Research” - Center for Democracy and Technology
Nuclear Power Plants: Efforts Made to Upgrade Security, but the Nuclear Regulatory Commission's Design Basis Threat Process Should Be Improved - UNT Digital Library

National Nuclear Security Threat Assessment, Design Basis Threats and Representative Threat Statements | IAEA

NNSA recognizes Design Basis Threat Implementation Team as 2020 Security Team of the Year | Department of Energy

Paris Bus. Prod. 04541, DocuGuard Standard Medical Security Paper, PRB04541, PRB 04541 - Office Supply Hut

The Bible Basis of Christian Security: Wakefield, Wesley H, Hale, D Curtis: 9780880195775: Amazon.com: Books

Security Situation in Asia Forms Basis of Global Security, Says President Tokayev - The Astana Times


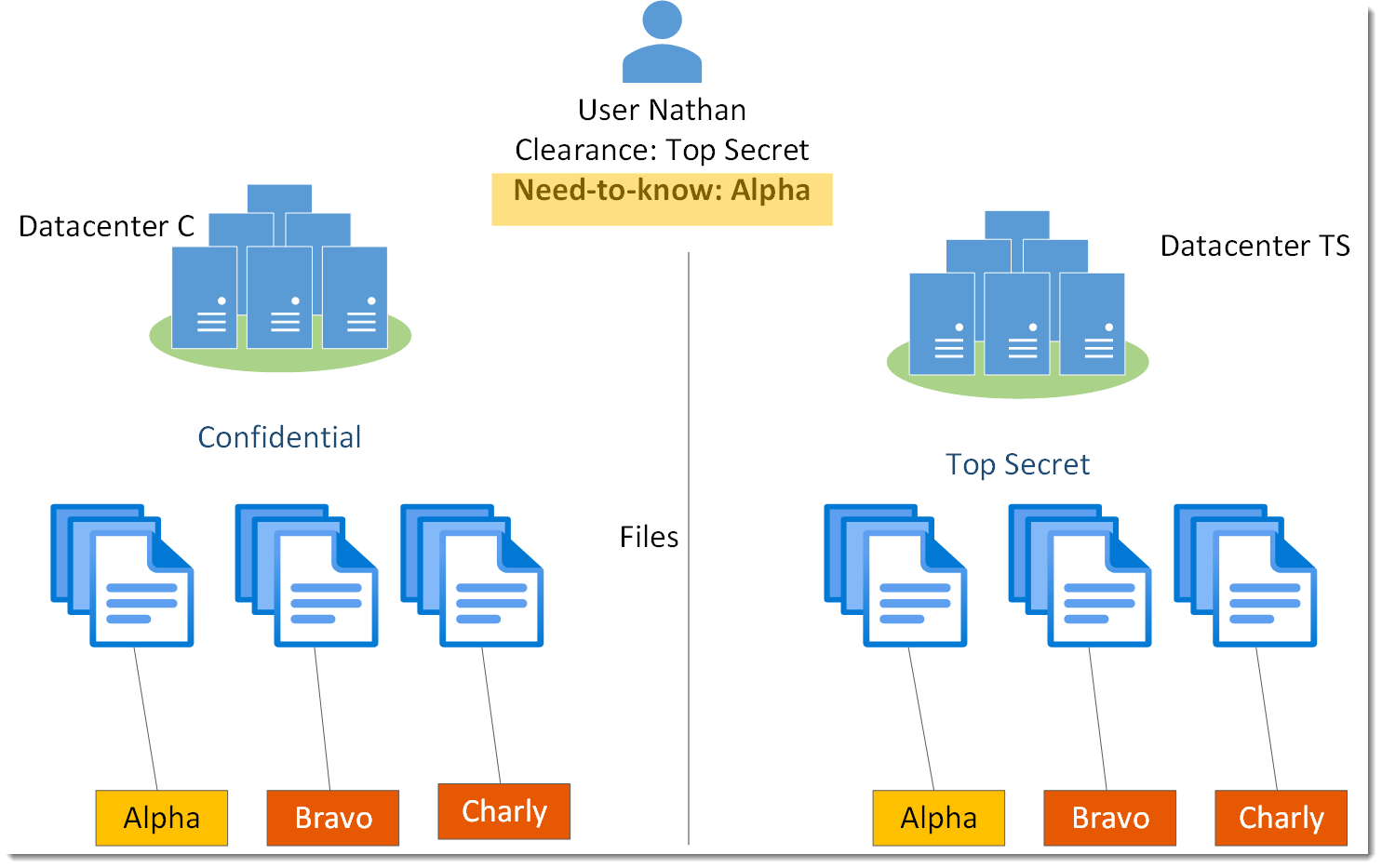





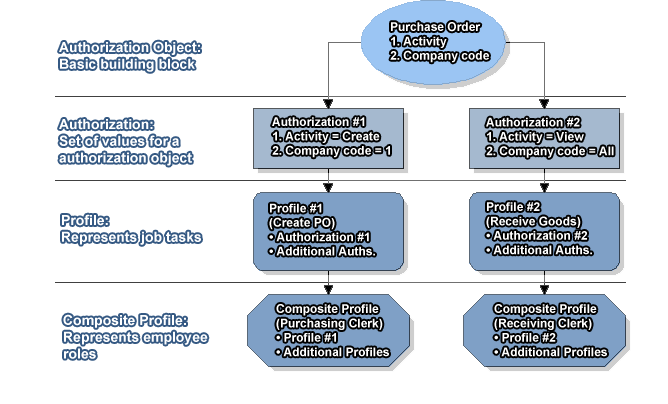







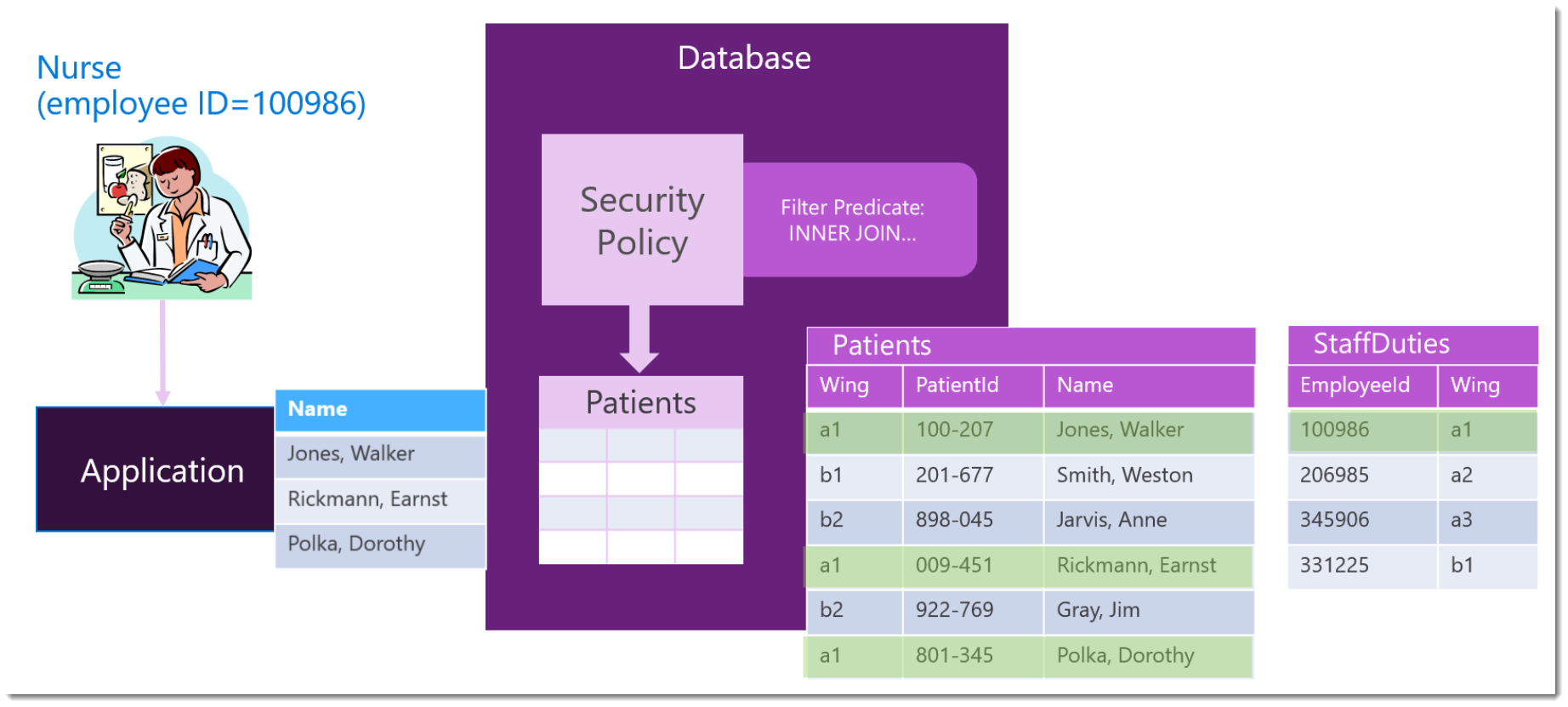
![PDF] Threat Modeling as a Basis for Security Requirements | Semantic Scholar PDF] Threat Modeling as a Basis for Security Requirements | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b1d4e1a34bf18501c0b1f54e5f1b3c06c2190e80/2-Figure1-1.png)